Blog Business Critical IT

19 Feb, 2020
We’ve all seen the glowing red Travelex boards in airports showing us the current rates for exchanging dollars. A recent report from the New York Times stated that on 31st December the lights went out on these boards due to a reported ransomware attack. Many banks which use Travelex to offer currency exchange services were also affected. This shows that even large corporations with large budgets for their security can still fall victim to determined hackers by underestimating their security requirements.

19 Feb, 2020
New Zealand's Computer Emergency Response Team (CERT) revealed that it's received the most incident reports for one quarter since it was established in 2017. An increase of 13% on the previous quarter. This shows that New Zealand is not immune to such attacks, and cybersecurity should be a priority both in your business and personally. To help you get a sense of the potential impact, a recent Newshub article showed how much an attack is likely to cost you. They also break down the different types of cybersecurity incidents being reported in New Zealand.

17 Jan, 2020
Vade Secure, a Predictive Email Defense company have released their Email Security Predictions for 2020. They have listed 6 ways they believe hacker swill target businesses over the next 12 months. Business email compromise (Spear Phishing) will be the main threat to businesses. Most of these are starting with very short emails saying something like, "Hello, are you available?". Click the link below to read more including their other predictions about sextortion emails, phishing links and data leaks. Predictions

17 Jan, 2020
Watch out for realistic phishing emails which are on the rise. Phishing emails are becoming more sophisticated and realistic with the main goal to trick you into clicking on a link that you shouldn't. Many of these are intercepted by your antivirus/antimalware software, however the clever crooks are always finding ways to get these emails to elude the filters. They will often use common respected brands to create an atmosphere of trust. These can include: Your subscription has expired Your payment was declined Someone is using your login You have an undelivered item which is being held at depot You have won something All we can advise is that you need to be extremely suspicious, hover over the link with your mouse. That should display the URL of the site and allow you to verify it is legitimate. If you think you have clicked on something you shouldn't, shut down the computer and call your friendly IT provider.

17 Jan, 2020
Having an enjoyable a holiday and immersing oneself in the festive season can cause some of us to take the eye off the ball and become complacent when it comes to cyber security threats. Unfortunately, the cyber criminals don't have that same Christmas loving and giving attitude and we can be certain that they have been beavering away in the background trying to find more devious and destructive ways to cause grief and losses to businesses in 2020. Some experts have claimed that the value of cyber-crime in 2018 was over US$1.5 trillion which is far greater than we thought and if this is correct, it will be substantially higher in 2020. With the escalating tension between Iran and the US, more cyber attacks from Iran are expected to be targeted at the US and her allies. Make one of your business New Years resolutions to upgrade your security systems so as to reduce the risk and impact of a cyber attack. Even with the best defences in place, people will always be the weakest link. We are human after all, we make mistakes and can be tricked into clicking on things we shouldn’t. The best form of defence for business owners is to train their staff to be able to know what is good and bad and to always be extremely vigilant. If you would like information on how to best train your staff on security awareness please get in touch.
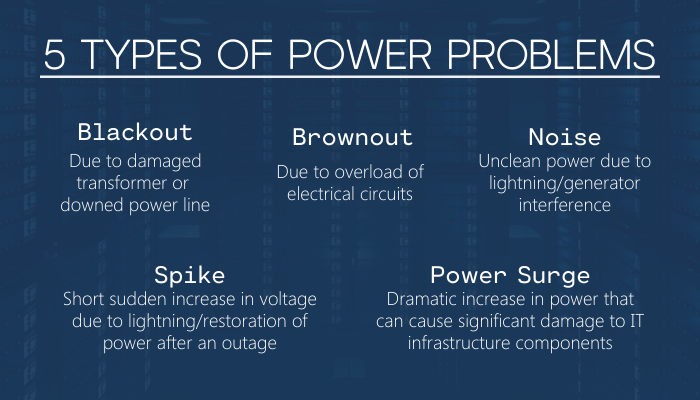
10 Dec, 2019
How often have you wished for an extra few minutes when the power goes out to give you the opportunity to save that document you’ve been working on all morning or complete a transactions on your Point of Sale machine? An Uninterruptible Power Supply (UPS) will give you those extra few minutes and lessening the impact the power going out has on your business. Additionally, a UPS protects your equipment from a variety of power problems. This including power spikes and power surges, which both have the potential to damage your electrical equipment, as well as keeping you running temporarily during a black or brownout to avoid damage or data loss by saving and shutting down. Please speak to us if you think a UPS could be useful to your business. We’ll help you get the right UPS for your needs.

10 Dec, 2019
KnowBe4 have recently released details about a new form of Phishing Attack. Users are receiving emails from HR which are offering better benefits or pay rises. That’s something we’d all like just before the holidays. These emails normally have a link which looks like a SharePoint document, but in fact it is a phishing landing page. Quite often phishing attacks spoof email addresses. At first glance it looks like it’s come from a legitimate source, maybe your HR manager. If you receive an email or phone call you feel is suspicious it would pay to call the person appearing to have sent the message. They will be able to confirm if they actually sent it to you. I nformation for this article was taken from KnowBe4

10 Dec, 2019
Many new business ventures start off with little or no complexity and few staff. The business owner has a concept that they believe will work, dreams up a company name and gets excited about designing a logo and business card. Depending on the product or service, they may already have developed a website and thought about email addresses. Typically, they begin working from home or small premises with an internet connection, basic email account, a mobile phone and tons of enthusiasm. Their computer is often a laptop with free antivirus and no backup solution. Systems are generally simple with and as they move through stages of "excited", "reality check", "somewhat hopeful", then to “Hey, this might be working!” Companies change as they experience growth, adding staff, purchasing specialised software solutions and requiring more from their hardware and network. As the complexity increases the business develops systems, procedures & policies to provide a level of control and monitoring. What we find, is with the increase activity and demands on the business owners time (and resources) their network and cyber security is often overlooked. This is why Computer Culture strongly recommend getting your IT provider involved at an early stage so that they can provide IT solutions that are scalable and adaptable to the businesses changing needs. These solutions will cover: Network design, device patching and user management Protection from viruses, malware and hackers Remote accessibility and setting up others to work remotely Data storage, protection and backup User cyber awareness training and education Disaster Recovery Plan Addressing these requirements involves an array of solutions with customisation for each organisation. Having regular reviews and sticking to upgrade cycles are important to maintain the level of protection. Please contact our sales team if you would like to know more about this assessment process.

22 Nov, 2019
It’s very easy to look at security as just protecting yourself from attacks from outside your own organization. The below article shows there are a lot of things we must think about with our internal staff and contractors. These threats can be either malicious or accidental. One very interesting statistic from SolarWinds shows 62% of businesses found insider mistakes were the leading cause of security incidents. Whether malicious or not, the result can be devastating to an organisation. The article focuses on two commonly overlooked security issues – employees who leave your organisation, and imposters who try to get passwords reset. Continue reading at the link below to see how these can happen and, more importantly, what can be done to help prevent these breaches. Source Article
Let us share our IT expertise to build your business success.
CALL US TODAY
+64 3 377 4662
FIND US AT
43 Moorhouse Avenue
Addington
Christchurch 8011
Addington
Christchurch 8011
© Computer Culture 2021- 2024, Registered in New Zealand No. 1981065. Site powered by Concilio
,


