Ransomware - heading your way in macro enabled Word documents
Recently we heard about a file containing a malicious macro (this is a small program, that once run expands into something larger) that Microsoft have flagged under a family of Trojan viruses that have been targeting MS Office software for several years.
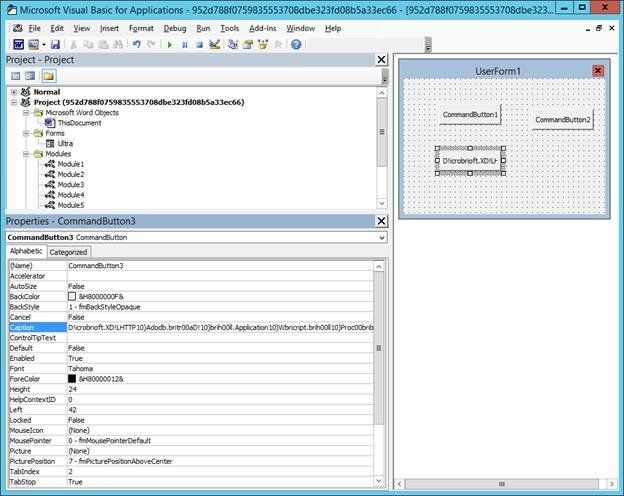
The problem was, there wasn’t an immediate, obvious identification that this file was actually malicious. It’s a Word file that contains seven VBA (Visual Basic for Applications – the programming language used within Office to develop Macros) modules and a VBA user form with a few buttons.
These modules appeared to be legitimate programs powered with a macro; no malicious code found there … However, after further investigation Microsoft noticed some anomalies within the macro. These anomalies cause the macro to connect to a URL and download a Locky ransomware payload.
This means the Locky virus will be downloaded to your PC if macros are enabled when opening the Word file in question.
We strongly suggest that to help prevent Office-targeting macro-based malware from infecting your system, you only enable macros if you wrote the macro yourself, or completely trust and know the person who wrote it.
As always, if you’re unsure about your system’s susceptibility to these attacks, or you would like some assistance preventing or dealing with this, please give us a call.